A few words of wisdom from someone who has seen more than her fair share of hacking attempts.
This morning, when I fired up my laptop after a weekend away with friends, I was greeted with an on-screen notification telling me that there was a problem with my iCloud account.
iCloud, in case you don’t know, is Apple’s cloud service. I use it for some email and to synchronize data among my three computers and three mobile devices. I generally don’t use any cloud storage for any sensitive documents. I simply don’t trust it.
Today’s notification prompted me to log into my iCloud account. When I tried to do so, an error message told me that the account had been locked due to too many incorrect password entries.
I do know my password and I know I hadn’t entered it wrong too many times. That means someone else had. Another hack attempt.
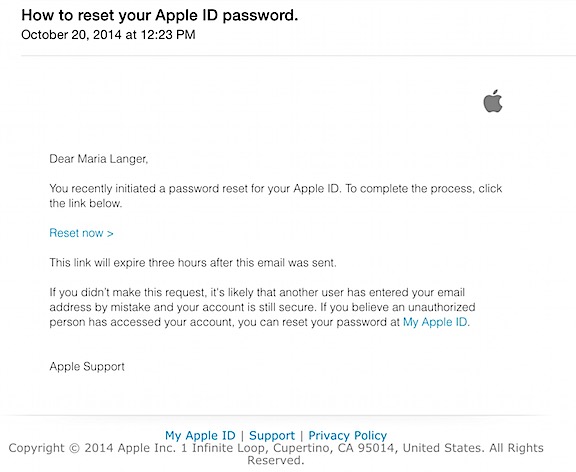
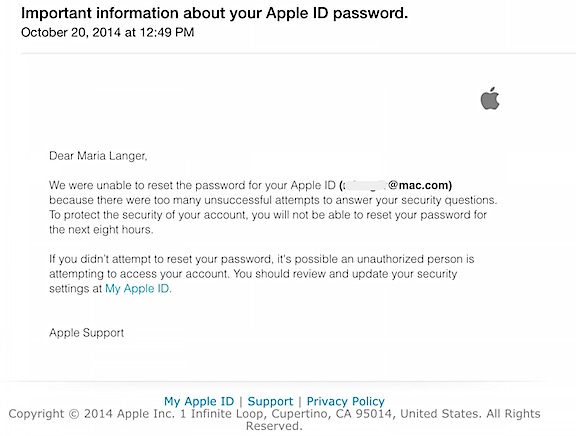
This isn’t the first time someone had tried so hard to hack into my iCloud account that the account had been locked. It also happened back in October 2014. I know this date because I blogged about it back then — and oddly enough, that’s the most popular blog post so far today. (Is someone looking for clues in my blog? Good luck with that.)
Anyway, I went to Apple’s website and logged into my account again. That required Apple to send an email message to my backup account and for me to click a link in that message. I normally don’t click links in any messages I get unless I’m expecting a message with a link. I was expecting that one so I clicked the link, signed back in, and checked to make sure everything was still secure. It was.
I then changed my password, just for good measure.
A Lost Phone Story
All this comes right on the heels of a rough weekend for a friend of mine.
We went out to run some errands in the Phoenix area where she lives. Our first stop was Lowe’s. She took out her phone to take a picture of something she wanted to compare with other options in other stores. Then she decided she wanted to sketch it instead. She put the phone down and took out a pad and pencil. I wandered off to look at other things. We later met up at check out, I paid for my purchase, and we left.
About a mile down the road, she declared, while searching frantically in her purse, that she was having a senior moment. She couldn’t find her phone. When she realized it definitely wasn’t there, she began to panic. She knew she’d left it in Lowes. I turned around and we headed back. She ran in. I waited two minutes, then called her phone as she’d asked me to.
It went right to voicemail.
I knew what that meant: someone had picked up her phone and turned it off so it couldn’t be tracked. Someone smart enough to do that wasn’t going to turn it in at Lost and Found. The phone was stolen.
I went into the store and gave her the news. I had to explain what the phone going right to voicemail meant — she was in a bit of denial before panic took root. “My life is in that phone,” she told me. I asked the question I already knew an answer for: was the phone locked? Did she have to enter a password it to use it? The answer was no.
Worse yet, she had used an unsecured “memo app” to record her passwords for banks, credit cards, and all kind of other important things. If someone opened that app, they’d have complete access to her finances.
My friend is not a technically minded person. She had no idea what to do. She asked me. I’m an Apple person and I know exactly what to do for an Apple device. But I was at a lost with her Samsung Galaxy 5. I called her husband, who I knew would know. But he’s an airline pilot and his phone was switched off for a flight.
We raced to the closest Verizon store. I repeatedly dialed her number and it immediately went to voicemail each time. That means the phone was still turned off. The average phone thief would not be able to get data off the phone with it turned off.
At the Verizon store, my friend used the tech guy’s computer to log into her Google account. He pushed the right buttons to wipe the phone clean and basically brick the phone.
Disaster (probably) averted.
The odd thing about all this is that although I’ve been keeping my phone locked for the past few years, lately it’s been bugging me that I need to go through that extra unlocking step to use it. I’ve been debating with myself for the past few weeks about removing the passcode and leaving the phone unlocked for my own convenience. I even came close to doing it once or twice.
But after seeing what happened to my friend, there’s no way in hell that I’ll remove the passcode on any of my mobile devices or computers.
And if your mobile devices aren’t secured with a password, take my advice and secure them now. And then make sure that your devices can be wiped remotely if needed.
Passwords
Whoever attempted to access my iCloud account recently hit a wall when he/she couldn’t enter the correct password. Apple automatically locked the account when a certain number of incorrect attempts — three? five? — had been made. The lock required me to recover it using a secondary email account or security questions.
Passwords are the first line of defense for security. We all want to use passwords that are easy to remember and we all want to use the same password for everything. Resist the temptation! If your password is easy to remember, it might also be easy to guess. And if you use the password for everything, if someone guesses one password, they automatically have access to everything you used it for.
Your passwords should not be easy to guess. Period. They should be a combination of upper and lowercase characters and numbers with one or two symbols thrown in whenever possible. Minimum password length should be eight characters; longer is better.

This is the most idiotic idea I’ve ever seen. Unless you plan on keeping this book locked up in a safe all the time, you’re just making it easy for a thief to access all of your accounts.
If you have trouble keeping track of your passwords, do not write them down in a place where other people can find them. That includes post-it notes, notebooks, and unsecured apps and documents on a computer or mobile device.
My wasband used to store all of his passwords in a Microsoft Word document that was not password protected. Then, as if that wasn’t dumb enough, he routinely emailed it as an attachment from one of his email accounts to another to get the file transferred between computers when he updated his passwords. He even did this after he knew that one of his email accounts had been breeched, thus giving the “hacker” access to all of his passwords everywhere. (And yes, I do constantly ask myself how I could have loved someone as stupid as he is.) For all I know, he probably still does this.
My advice? Instead of insecurely storing this information, invest a few bucks in a password security app. I use 1Password, which works on my Macs and iOS devices, keeping all of my passwords synced between them. (There are plenty of other options out there; feel free to suggest your favorite in comments for this post.) To access my passwords, someone needs to first get into my computer or device (which is password protected) and then open the 1Password app (which is password protected with a different password).
Don’t give your passwords to anyone — even someone you trust. A long time ago, when I was a lot less security-minded, I had a simple password I used for most (but fortunately not all) things, including my Netflix account. My idiot wasband, while we were still married, gave that Netflix password to his roommate. Fortunately, he did this right in front of me so I knew about it. (Let’s not go into how pissed off I was.) I spent a good portion of that day changing my password everywhere it might be used. Needless to say, I never gave him any of my passwords again — which served me well when the divorce proceedings started and I had assets to protect.
Security Questions
Security questions are the next line of defense. They help protect your account while giving you access to it if you happen to forget the password. It’s the security questions that protected my iCloud account back in October 2014; someone had actually tried to answer them and failed.
After my recent iCloud hack attempt, I checked and changed a few of my security questions. I was very pleased to see that Apple offered questions that dug deep into my past, with answers that only I would know. Mother’s maiden name is the last question you should select and answer — it’s too widely used. So is where you and your spouse met — how many times have you told that story? (And of course, your spouse knows the answer, which can come back to bite you when divorce papers are filed.) Always pick questions that are easy for you to answer but damn near impossible for anyone else to figure out.
Of course, there is a more devious way to handle security questions and that is to use the same password as the answer to all of them. So while the question might ask “What is your father’s middle name?” — a question that anyone who knows you can research to discover — the answer might be “Jj6MbFwp,” which is obviously not your father’s middle name. That same password would then be the answer to all of your other security questions. So while your ex is trying to figure out why the system isn’t accepting “John” for the father’s middle name question when he knows damn well the name is John, you’ve fooled him by using something he’d never guess in a million years.
Which approach did I use? I won’t tell.
Take Security Seriously
Computer and Internet security — is not something to be taken lightly. The more connected you are and the more you access your personal information and finances online, the more at risk you are for loss if someone is able to access an account. It’s only by having good, difficult-to-guess passwords for your accounts — and making sure you have different passwords for each account — that you can keep them safe.
And remember, your smart phone is likely to be more valuable to a thief than your wallet. Protect it!